HOME Information DrayTek Blog Security Ways to Improve Network Security
Ways to Improve Network Security
This article introduces some protections you can take on your Vigor Router to keep the network safe, including how to block unauthorized users, as well as what protecting the local network from the threats on the Internet.
DrayOS 5
Keep your network safe and reliable with Vigor Router’s built-in protections. From replacing the default admin account with your own secure credentials, to blocking unauthorized access, and shielding your local network from Internet threats — DrayOS5 Vigor Router gives you the tools to stay protected with confidence.
Router Security Protection
1. Create a Unique Administrator Account
DrayOS 5 allows users to disable the default administrator account for WAN access. It is strongly recommended to create a unique administrator account via IAM / Users & Groups and use it for router management. Disabling the default account and using a new one significantly increases security.
2. Use a Strong Password and Enable Two-Factor Authentication for Remote Access
Many routers on the market use the same default password for the management interface, making them easy targets. Vigor Router requires users to change the admin password upon first login.
Make sure to choose a strong, secure password as the router’s login password.
To enhance remote access security, enable Two-Factor Authentication (2FA). This adds an extra verification step beyond the administrator password. You can: Follow the guide "Use 2-Step Authentication for Remote Access" to set up 2FA via an Auth-Code sent to a specified recipient.
Use TOTP (Time-based One-Time Password) by setting up an authenticator app that generates a unique code each time you log in. Refer to "Use TOTP for Remote Access" for setup instructions.
3. Keep Firmware Up to Date
Always use the latest firmware version on your Vigor Router to ensure all security patches and new features are applied. You can enable automatic firmware upgrade feature on the router, which allows it to check for and install new versions automatically.
For manual updates, download the latest firmware at:
https://www.draytek.com/support/resources?type=version
4. Set Up an Access List for Management Access
When remote management is enabled, using an Access List is highly recommended. This feature restricts access to the router's management interface to trusted IP addresses only.
Vigor Router supports pre-defined IP Objects, IP Groups, and Hostnames in the Access List, making it easier to configure and manage.
5. Disable Unused VPN Services
VPN ports remain open as long as VPN services are enabled. If you're not actively using these services, it's best to disable them to reduce the potential attack surface.
6. Change the Default Management Ports
Vigor Routers use standard ports for web and CLI access by default, making it easy for LAN clients or attackers to find the management page. Change these ports via System Maintenance >> Management to make unauthorized access more difficult.
7. Enable Brute Force Protection
Attackers may attempt to guess your login credentials by trying multiple combinations (a brute-force attack). Enable Brute Force Protection to block IP addresses that have failed too many login attempts. This introduces a penalty delay, making brute-force attacks far less effective.
8. Use Port Knocking to Secure the Management Interface
When service ports are open, they can be targeted by attackers. Enable Port Knocking under System Maintenance >> Management to keep all ports closed until a correct sequence of port access attempts (a “knock”) is made. This sequence acts as a password, only opening the ports to those who know it.
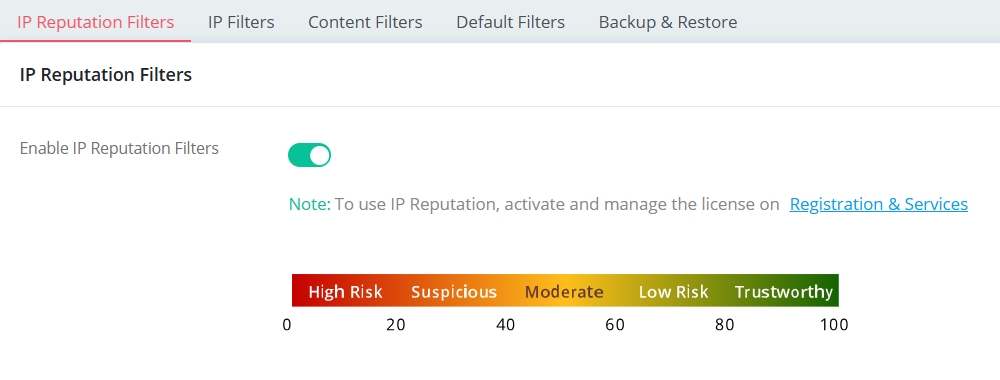
9. Use IP Reputation to drop the access from the bad score IP.
With the URL Reputation license, Vigor Router provides IP Reputation function, which can check the reputation score of incoming IP addresses. Connections from IPs with poor reputation can be automatically blocked to enhance security.
Local Network Security
Implementing VLAN for guests
Setting up VLAN on the local network allows you to isolate the guest from the private network while providing Internet connectivity to them. Also, the support of multiple subnets allows the private network and guest network to be on different IP subnets and have separate DHCP settings or policies.
If you have a VLAN capable switch on the network, you can follow the guide Use Multiple LAN Subnets with Tag-Based VLAN to set up VLAN on Vigor Router. The multi-SSID of VigorAP can be mapped to different VLAN as well, see Add a Separate Wireless Network for Guests for more details. If there’s no VLAN-capable switch nor AP, Vigor Router can also do port-based VLAN, visit Use Multiple LAN Subnets with Port-Based VLAN for instruction.
Disable DHCP server and change the LAN IP
For a device to communicate with the router, it needs to use an IP address in the same subnet as the router. While DHCP function is enabled, the router will automatically assign a valid IP address to the device connected to the network. If you don't want un-authorized hosts to access the network, you can disable the DHCP server, and manually configure the IP on authorized hosts. You might also want to change the LAN IP range as well, so it is more difficult for the un-authorized hosts to find out the IP range. The IP and DHCP settings can be configured at Configuration / LAN.
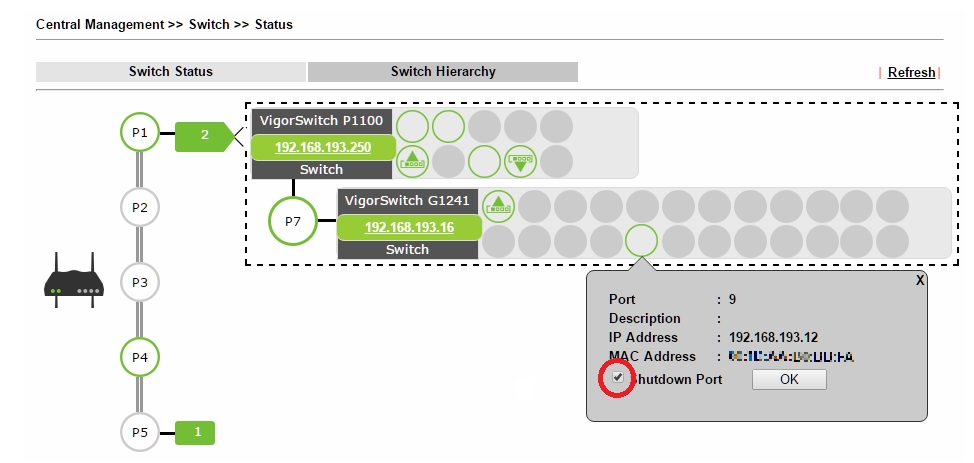
Shut down the unused ports on the switches
An open Ethernet port gives rogue devices access to the private network; therefore, make the ports not-in-use are disabled in the Switch configuration. If you are using a Vigor Router that supports SWM (Central Switch Management) along with VigorSwitches, you can view the Switch's port status from the router's management page and shut down an unused port directly.
Wireless Network Security
Use WPA3/WPA2 security mode
Since the wireless traffic is sent over the air, it can be eavesdropped by anyone nearby; therefore, be sure to apply security settings for encrypting the traffic, as well as controlling the access to the local network. Among WEP, WPA, WPA2 and WPA3, WPA3 is the strongest security protocol and is what we recommend to use.
Use 802.1X authentication (WPA2-Enterprise)
PSK (Pre-shared Key) authentication cannot manage individual users. If someone let out the password accidentally or intentionally, Network Administrator would have to change the password for everyone to revoke the Wi-Fi access. To manage the Wi-Fi access more efficiently, 802.1X authentication, which requires every user to log in with a unique username and password, would be a better option.
To deploy 802.1X authentication, you will need a RADIUS server to maintain the user database and verify the credentials. If you don’t have a RADIUS server on the network, that’s no problem, both Vigor Router and VigorAP support built-in RADIUS server. See Use the Router's Internal RADIUS Server for 802.1X Authentication and Use VigorAP As a RADIUS Server for implementing 802.1X authentication with the built-in user database.
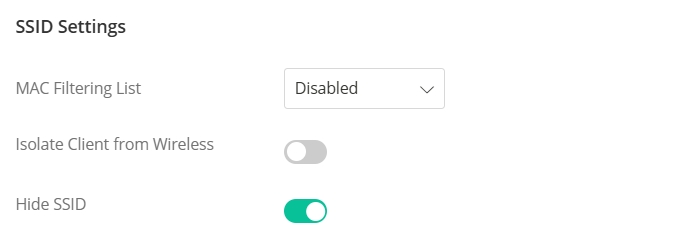
Hide SSID
Toggle “Hide SSID” in Configuration / Wireless LAN page, for the router/AP to stop broadcasting the existence of the wireless network so that only the users who know the SSID can gain access to the network.
Internet Access Security
Apply IP Filter
You may use Vigor Router’s built-in Firewall to manage both outgoing and incoming traffic, set up rules to block the LAN clients from using vulnerable services, or restrict the local server to some particular Internet IP addresses only. See Block FTP Service by Firewall for an example.
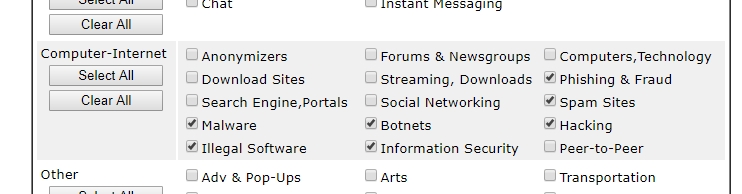
Block Access to Malware by Content Filter
Set up URL Keyword Filter to block the local client from accessing the websites that are associated with malware. Web Content Filter is also a great solution which helps the router to filter malicious websites automatically and allows you to block all of them without identifying every URL.
Block Access to/ from IP with poor Reputation
Vigor Router works with the URL Reputation Server’s database to assess the credibility of IP addresses based on past activities such as spam, malware, or phishing. Connections to or from IPs with low reputation scores are automatically blocked, reducing attack risks and protecting network resources.